Understanding the Importance of Blockchain Security
With over $4.1 billion lost to DeFi hacks in 2024 alone, the importance of robust blockchain security cannot be overstated. In the rapidly evolving world of cryptocurrencies, ensuring the security of digital assets is essential for both investors and platforms. The method of auditing security, especially through HIBT security audit methodology, offers a complete framework for protecting digital assets.
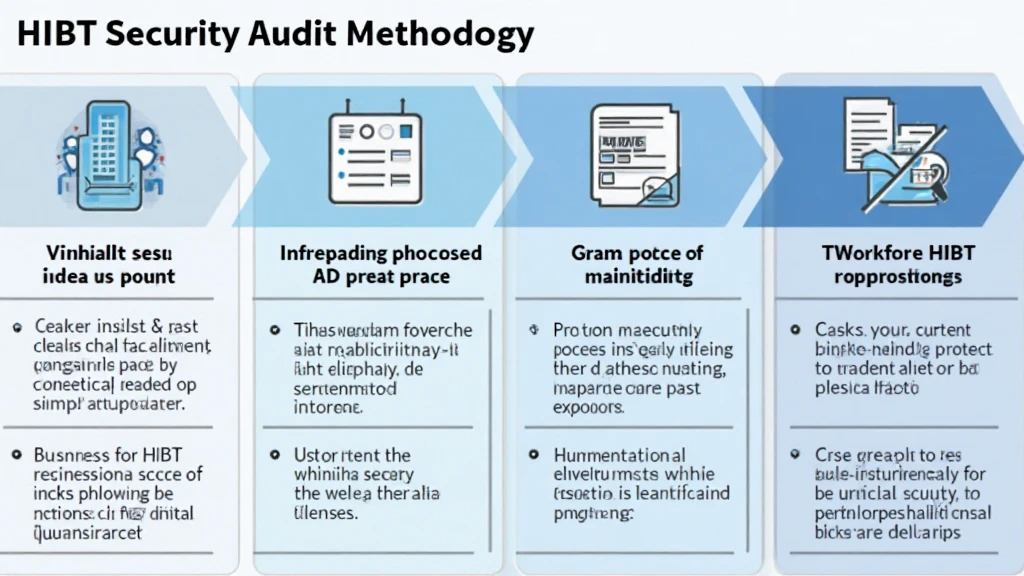
What is HIBT Security Audit Methodology?
The HIBT (High Integrity Blockchain Technology) security audit methodology provides a systematic approach to evaluating the security of blockchain systems. This methodology involves a series of phases, each aimed at identifying vulnerabilities within blockchain architectures and smart contracts.
Core Phases of HIBT Security Audit
- Phase 1: Initial Assessment – This involves a thorough review of the blockchain’s framework and its implementation.
- Phase 2: Risk Analysis – Identifying potential attack vectors and assessing their impact on the system.
- Phase 3: Code Review – A line-by-line evaluation of smart contracts and associated code.
- Phase 4: Penetration Testing – Simulating attacks to test the resilience of the smart contracts.
- Phase 5: Reporting – Documenting vulnerabilities and providing actionable recommendations.
Why is HIBT Effective?
In contrast to traditional auditing methods that may overlook specific nuances in smart contract operations, HIBT integrates advanced techniques and industry benchmarks to ensure a more thorough evaluation. This is particularly beneficial as the industry faces increasing scrutiny and regulations aimed at securing digital assets.
Blockchain Vulnerabilities: Consensus Mechanism Vulnerabilities
When it comes to understanding blockchain technology,one of the most critical elements is the consensus mechanism. Different blockchain networks implement varying consensus algorithms, such as Proof of Work, Proof of Stake, and others. Each has its own set of vulnerabilities that can be exploited if not properly secured.
How Vulnerabilities Can Affect Users
Imagine a bank vault; if the lock is outdated, it becomes an easy target for thieves. Similarly, if a blockchain’s consensus mechanism is flawed, it can lead to a breach of trust and loss of funds. For instance, vulnerabilities in Proof of Work systems can be exploited through 51% attacks, allowing malicious actors to manipulate transaction confirmations.
Legal Compliance and Security Standards in Vietnam
The Vietnamese cryptocurrency market has seen significant growth, with a 150% increase in active users since 2022. As more individuals participate in trading and investing, compliance with local security standards becomes crucial. Vietnam’s cybersecurity regulations echo the international trends, often reflecting the growing need for better auditing processes like HIBT.
Vietnamese Compliance Trends
As the local market evolves, here are some trends seen in compliance:
- Increase in regulatory frameworks for blockchain companies.
- Mandatory audits for financial transactions involving cryptocurrencies.
- Emphasis on security compliance for DeFi projects.
How to Audit Smart Contracts Effectively
Auditing smart contracts is a nuanced process that requires specific skills and knowledge of coding, security standards, and blockchain operations. Utilizing tools like MythX and Slither can enhance effectiveness in identifying vulnerabilities.
Steps for Smart Contract Audits
- Understand the Contract Functionality – Grasp the intended functionality and its implications.
- Utilize Automated Tools – Employ tools for initial code scans.
- Conduct Manual Reviews – Focus on critical algorithms and business logic.
- Test for Edge Cases – Ensure contract behavior is consistent across various situations.
- Feedback Loop – Engage with stakeholders for insights and improvements.
Real-World Data: The Impact of Poor Security
Data shows that most successful hacks involve poorly audited smart contracts. For instance, leading analytics firm Chainalysis reported that 80% of all DeFi exploitations happened due to flawed security assessments in 2023.
Conclusion
As we move into 2025, the importance of the HIBT security audit methodology will only increase. For investors and platforms alike, understanding how to secure digital assets effectively is paramount. Just as a proper security system protects a physical asset, HIBT methodology serves as a digital fortress for blockchain systems.
In conclusion, as the Vietnamese market embraces blockchain technology, it becomes crucial for both emerging and established platforms to adhere to rigorous security audits. HIBT offers an innovative framework to ensure the safety and integrity of digital assets, supporting a vibrant and secure cryptocurrency landscape.