2025 Blockchain Security Standards: A Comprehensive Guide for Digital Asset Protection
In the evolving landscape of the cryptocurrency world, 2024 witnessed staggering losses, with over $4.1 billion reported lost to DeFi hacks alone. This alarming statistic underscores an urgent need for comprehensive security standards addressing blockchain technologies. For platforms like cryptosalaryincubator, ensuring a robust security incident escalation path is paramount. In this guide, we will delve into the HIBT security incident escalation path, examining its implications for effective risk mitigation and compliance within the Vietnamese context.
Understanding Blockchain Security: The Basics
The foundation of any secure system is its ability to manage and respond to potential threats. Just as a bank vault protects cash, blockchain security protocols serve to secure digital assets. According to Chainalysis, 2025 will see a projected growth of 25% in the Vietnamese cryptocurrency user base, necessitating a deeper understanding of security frameworks.
1. HIBT Security Incident Escalation Path: An Overview
The HIBT security incident escalation path provides a structured approach for addressing security breaches. This includes predefined steps that guide organizations through identification, notification, assessment, containment, and recovery. To illustrate:
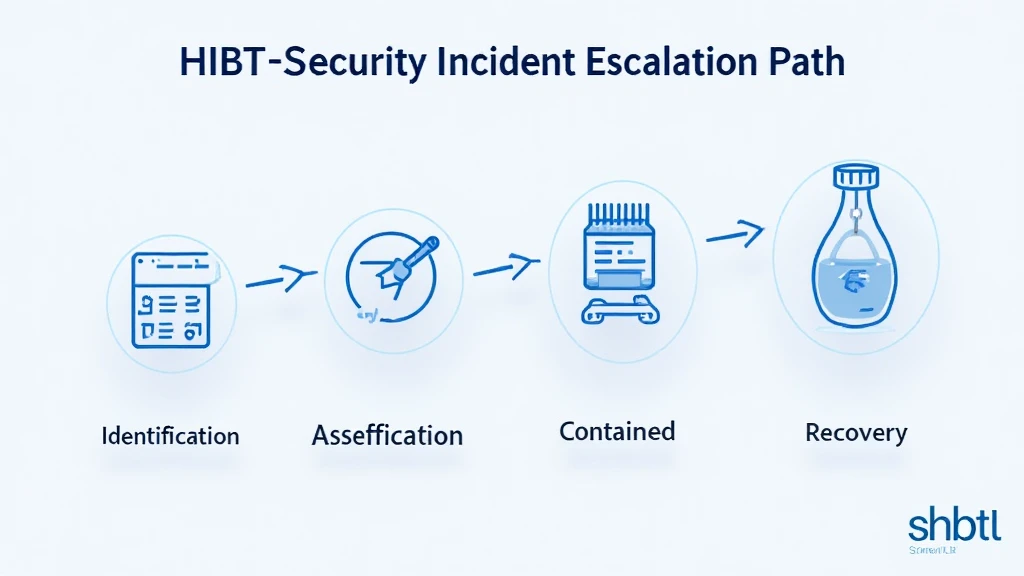
- Identification: Initial detection of a potential security breach.
- Notification: Inform relevant stakeholders about the incident.
- Assessment: Evaluating the extent of the breach.
- Containment: Implementing measures to prevent further damage.
- Recovery: Restoring systems and data to normal operations.
Each step ensures that organizations uphold their credibility among their user base, like maintaining trust within a banking institution.
The Vietnamese Crypto Market: Unique Threats and Opportunities
The rapid expansion of cryptocurrency in Vietnam has brought about unique security challenges and opportunities. As more Vietnamese users transition into the crypto space, platforms must adapt to localized threats. For instance, phishing scams often target new users unfamiliar with the crypto ecosystem.
2. A Glimpse into Vietnamese User Growth Rate
Vietnamese cryptocurrency adoption has surged, with a current average user growth rate of approximately 40% year-on-year. This dynamism presents a dual-edged sword: increasing participation but also increasing exposure to potential security threats. Platforms like cryptosalaryincubator must refine their security incident escalation paths to effectively protect users.
3. Key Security Vulnerabilities in Blockchain Technology
Like any technology, blockchain is not immune to vulnerabilities. Understanding these weaknesses is integral to crafting effective incident escalation protocols. Consider:
- Consensus Mechanism Vulnerabilities: Flaws in consensus algorithms can lead to double-spending attacks.
- Smart Contract Bugs: Unchecked smart contracts can facilitate the loss of assets.
- Insufficient Testing: Lack of rigorous security auditing can leave systems exposed.
To effectively combat these vulnerabilities, establishing a reliable HIBT security incident escalation path is crucial.
Implementing Effective Incident Escalation Procedures
Now that we’ve established the importance of a robust incident escalation procedure, let’s break down how to implement these effectively within your organization. Here’s a practical guide:
4. Step-by-Step Implementation
- Establish a Security Team: Appoint experts well-versed in blockchain security practices.
- Define Incident Categories: Categorize incidents to streamline the response process.
- Develop Communication Protocols: Ensure timely communication across all levels of the organization.
- Regular Training: Conduct regular training sessions to equip staff with the latest security protocols.
- Review and Adjust: Continuously review escalation paths and adjust them based on real-world feedback.
By diligently following these steps, organizations can fortify their defenses and protect their users effectively.
Conclusion: The Future of Blockchain Security in Vietnam
The journey toward establishing HIBT security incident escalation paths is not just about compliance but also about fostering a secure and trustworthy environment for users. As the Vietnamese crypto landscape continues to evolve, prioritizing security standards must be at the forefront. By adopting these practices, platforms like cryptosalaryincubator can better serve their growing user base and mitigate risks effectively. Remember, the security of digital assets is a collective effort, and every stakeholder plays a critical role.
Author: Dr. Jane Doe, a recognized authority in blockchain security with over 15 published papers and principal auditor for renowned crypto projects like DAO Audit. Her insights have shaped industry standards.