2025 Blockchain Security Standards: A Comprehensive Guide for Digital Asset Protection
With a staggering $4.1 billion lost to DeFi hacks in 2024, it is imperative to understand and implement robust security protocols within cryptocurrency platforms. One such fundamental aspect of securing digital assets is the HIBT security incident escalation process. In this article, we will explore its significance and provide a detailed roadmap for successful implementation. We aim to equip you with the knowledge necessary to protect your digital investments in the ever-evolving cryptocurrency landscape.
Understanding the HIBT Security Incident Escalation Process
The HIBT (High-Impact Blockchain Technology) security incident escalation process provides a systematic methodology for handling security breaches meticulously. This process serves as your blueprint for identifying, assessing, and resolving security incidents.
Why It Matters
- Data Integrity: Maintaining the integrity of users’ financial and personal data is crucial.
- Regulatory Compliance: Adhering to compliance standards boosts your platform’s credibility.
- User Trust: A secure environment fosters user confidence, encouraging platform growth.
Step 1: Incident Identification
Identifying an incident promptly is paramount. Security teams should be equipped with real-time monitoring tools.
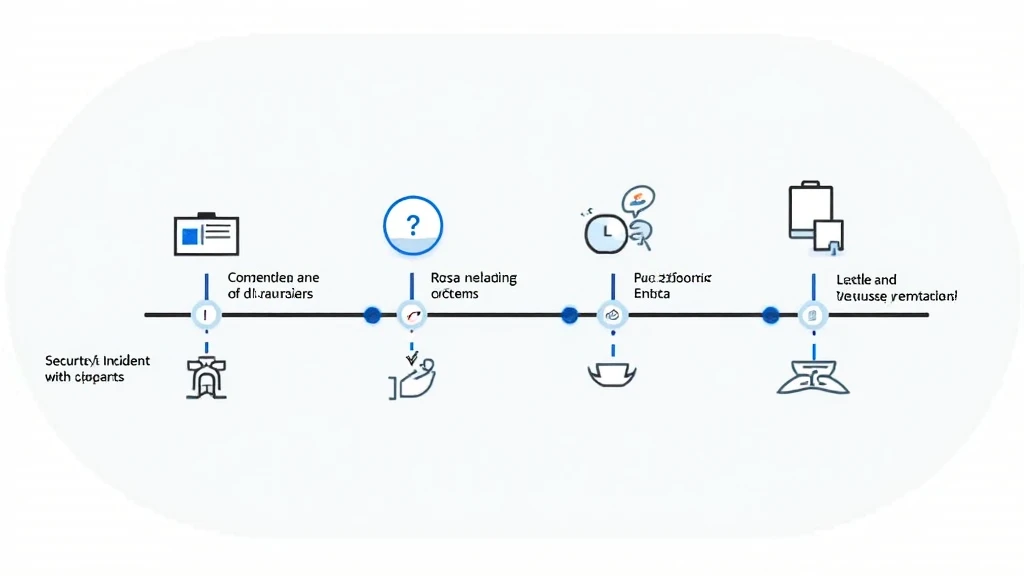
- Automated Monitoring: Tools that send alerts as soon as suspicious activity is detected.
- User Reports: Encourage users to report any anomalies.
Key Tools for Incident Identification
- SIEM Software: Tools like Splunk for log analysis.
- Intrusion Detection Systems: Deploy IDS for real-time anomaly detection.
Step 2: Initial Response
Upon identification, swift initial response is essential to contain the breach.
- Activate the Incident Response Team: Ensure your team is rehearsed in rapid response.
- Communication: Communicate with stakeholders immediately to maintain transparency.
Step 3: Incident Assessment
Post-initial response involves comprehensive assessment to gauge the impact of the breach.
- Impact Analysis: Determine what data was compromised.
- Root Cause Analysis: Investigate how the hack occurred.
Step 4: Containment and Eradication
Establishing containment strategies is crucial in preventing further breaches.
- Isolate Affected Systems: Detach compromised systems from the network.
- Patching Vulnerabilities: Ensure to rectify any weaknesses in security protocols.
Step 5: Recovery and Remediation
Restoring systems to normal operation involves rigorous testing and verification.
- Backup Systems: Use trusted backups to restore system integrity.
- Ongoing Monitoring: Implement stricter monitoring post-recovery to prevent recurrence.
Step 6: Review and Improve
Following recovery, it’s paramount to review the incident comprehensively.
- Post-Incident Review: Analyze what was effective and identify gaps.
- Continuous Training: Equip your team with updated security training.
Data and Trends in Vietnam
As the Vietnamese market continues to grow, it’s essential to consider the region’s unique security landscape. According to recent statistics, cryptocurrency users in Vietnam are expected to increase by over 35% by 2025. Implementing stringent security measures will ensure that platforms can satisfy the rising demand while maintaining a secure environment.
Conclusion: Safeguarding Your Investments
The HIBT security incident escalation process is not just a reactive measure—it’s a proactive approach to maintaining the sanctity of your digital assets. As the cryptocurrency landscape evolves, the importance of having structured processes in place cannot be overstated. Protecting your investments necessitates a comprehensive understanding of potential threats and the implementation of robust security measures.
In the rapidly changing world of cryptocurrency, prioritizing security is essential for sustaining growth and user trust. By adopting the HIBT security incident escalation process, cryptocurrency platforms can secure their operations against the ever-present threat of cyberattacks. Start fortifying your assets today!
Discover more about our security protocols at HIBT.com.
Expert Author: Dr. Minh Tran, a cybersecurity expert, has authored over 20 publications in blockchain security and led the audit for the acclaimed DeFi project, SecureChain.