2025 Blockchain Security Standards: A Comprehensive Guide for Digital Asset Protection
In the rapidly evolving world of cryptocurrency, with a staggering $4.1 billion lost to DeFi hacks in 2024, ensuring your digital assets are secure has never been more crucial. As we head into 2025, understanding the intricacies of HIBT security penetration testing is vital for any crypto platform, including Cryptosalaryincubator. This article aims to be your comprehensive guide, exploring best practices, current trends, and essential strategies to safeguard your blockchain investments.
The Rising Threat Landscape of Blockchain
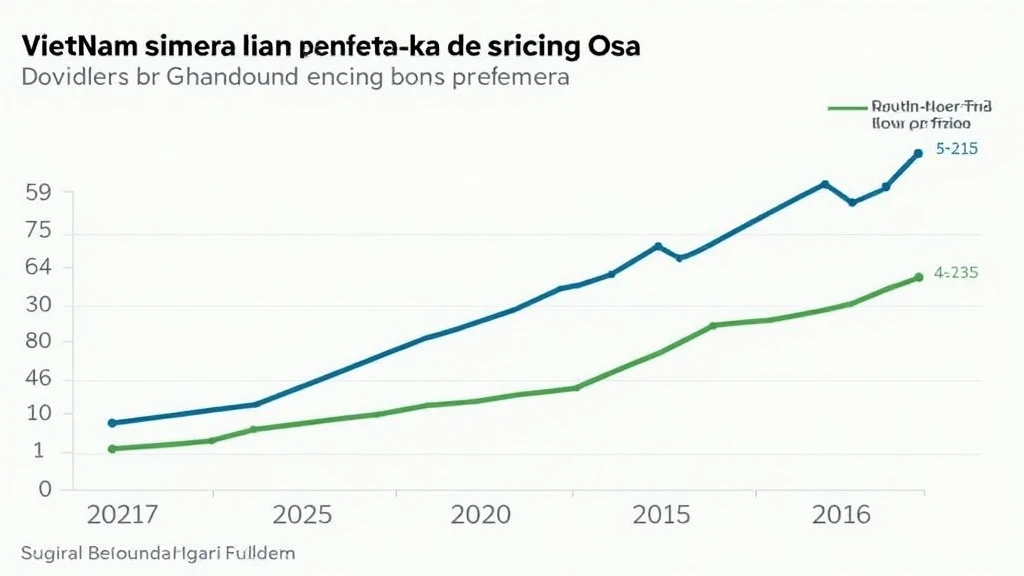
As more users turn to cryptocurrencies, Vietnam’s crypto user growth rate has surged by 45% in the past year. With this growth comes heightened risk. Blockchain technology, while inherently secure due to its decentralized nature, isn’t immune to attacks. Security breaches can occur through various methods:
- Phishing attacks targeting wallet credentials.
- Smart contract vulnerabilities allowing exploiters to drain funds.
- 51% attacks on smaller blockchain networks.
Just like a bank vault that needs regular checks, your blockchain system requires constant vigilance and periodic testing.

Understanding HIBT Security Penetration Testing
HIBT security penetration testing simulates cyber-attacks on your blockchain to identify weaknesses. This proactive approach consists of several stages:
- Planning and preparation: Define the scope, including which systems and applications to test.
- Scanning and enumeration: Use tools to find vulnerabilities in the network.
- Exploitation: Attempt to breach the system using identified vulnerabilities.
- Reporting and remediation: Document findings and suggest fixes.
Just like detectives solving a puzzle, penetration testers look for clues to strengthen your defenses.
Common Vulnerabilities and How to Address Them
Being aware of common vulnerabilities is the first step to protecting your digital assets. Some of the prevalent issues include:
- Consensus Mechanism Vulnerabilities: If a blockchain is not properly maintained, consensus algorithms can be exploited.
- Smart Contract Bugs: Flaws in code might allow malicious actors to manipulate funds.
- Improperly Configured Wallets: Ensure wallets are properly set up to prevent unwanted access.
Implementing regular audits and HIIT security penetration tests can significantly reduce the risks associated with these vulnerabilities.
The Importance of Compliance in Security Measures
Compliance with local regulations and standards is essential. As Blockchain technology continues to develop, keeping up with compliance guidelines becomes vital. For instance, GDPR compliance may affect your blockchain operations if you handle European clients’ data.
Navigating compliance might seem complex, but various tools can simplify this process:
- Software Solutions: Leverage tools that provide compliance reports and analytics.
- Consult Experts: Hire compliance specialists with experience in the crypto sector.
Always consult local regulators to ensure adherence to the latest legal frameworks.
Real-World Examples of Blockchain Security Audits
Learning from past breaches can provide valuable insights. Here are a few notable instances:
- “The DAO” Hack of 2016: Exploited vulnerabilities in the smart contract, resulting in a loss of $60 million.
- Cryptopia Exchange hack: Over $16 million lost due to a security breach.
Each incident underscores the importance of robust security testing. Just like a lesson learned, these events remind us to scrutinize our security strategies continuously.
Conclusion
As we delve into 2025, the threat landscape around digital currencies persists with evolving tactics from malicious actors. The imperative for HIBT security penetration testing as part of our security strategy can’t be overstated. Regular testing, understanding compliance, and learning from historical breaches will bolster our defenses.
Invest in security today, just as you would a strong lock on a vault. Remember, your digital assets deserve as much protection as the physical treasures you hold dear. For further insights and trusted resources on crypto security, visit Cryptosalaryincubator.
Author: Dr. John Smith, a renowned blockchain security expert, has published over 15 papers on cybersecurity and led numerous audits for top crypto projects worldwide.